Introduction
Data integrity is the foundation of every successful ERP implementation. When information flows seamlessly across modules without duplication, inconsistency, or human error decision-making becomes faster and more accurate. In the Epicor ERP system, Business Process Management (BPM) tools are one of the most effective ways to enforce rules, validate inputs, and ensure quality control across departments.
In this post, we’ll explore practical strategies for using Epicor BPMs to maintain data integrity across multiple ERP modules. Whether you’re managing inventory, processing sales orders, or handling finance operations, this guide will help you create a more robust, error-resistant ERP system.
Why Data Integrity Matters in Epicor ERP
ERP systems like Epicor are built on interconnected modules. A single piece of incorrect data in one area can cascade into multiple downstream issues, such as:
- Incorrect inventory levels affecting order fulfillment
- Financial reporting errors due to inconsistent GL postings
- Customer satisfaction issues from inaccurate shipping details
Maintaining data integrity means ensuring that all entries are accurate, consistent, and validated at the point of input. Epicor BPMs are uniquely suited to this task.
What Are Epicor BPMs?
Epicor BPMs are configurable business rules that monitor and control how data flows through the ERP system. These rules can be attached to methods, tables, and triggers, and they run either before or after data is processed.
There are two primary types of BPMs:
- Method Directives – Triggered during process execution (e.g., Sales Order creation)
- Data Directives – Triggered when data changes in a table (e.g., new record inserted into Customer table)
By leveraging BPMs, organizations can implement validation, automation, and alerts without needing custom code.
1. Identify Key Cross-Module Integrity Risks
Start by evaluating where your data flows between modules and where errors commonly occur. Focus on:
- Manual data entry points
- Interfaces between modules (e.g., Sales to Inventory)
- Integrations with third-party systems
- Fields that are reused in multiple places (e.g., Customer ID, Part Number)
Common scenarios where data integrity can break down:
- A part is sold but not flagged as active in inventory
- A GL account is assigned incorrectly due to inconsistent setup
- A purchase order is approved without matching supplier terms
2. Use Pre-Processing BPMs to Validate Input
Pre-processing BPMs execute before a transaction completes, making them ideal for validation.
Example Use Case: Validating Customer Credit Limit in Sales Order
Module: Sales Order Entry
Objective: Prevent users from creating a Sales Order if the customer has exceeded their credit limit.
BPM Action:
- Use a Condition to check current AR balance
- Raise an exception with a user-friendly message if over the limit
Why This Works
This validation protects both the Sales and Finance modules. It prevents revenue forecasting errors, reduces risk, and ensures Sales reps stay aligned with financial policies.
3. Use Post-Processing BPMs to Sync or Alert Other Modules
Post-processing BPMs trigger after a transaction is completed. These are ideal for:
- Sending alerts
- Updating related records in other modules
- Triggering workflows in downstream processes
Example Use Case: Auto-Update Inventory Allocation After Order Confirmation
Module: Sales Order
Objective: When an order is confirmed, update inventory allocations immediately.
BPM Action:
- Trigger inventory check
- Allocate available stock
- Notify the warehouse if allocation is insufficient
4. Use Data Directives to Enforce Table-Level Consistency
While method directives handle business logic, data directives work directly on database tables, making them ideal for core data validations.
Example Use Case: Enforcing Required Fields for Vendor Records
Module: AP / Suppliers
Objective: Ensure that all vendors have tax IDs before saving.
BPM Action:
- Add a standard data directive on the Vendor table
- Use Conditions to check the Tax ID field
- Block saving if missing
This ensures Finance and Procurement work with fully compliant vendor records.
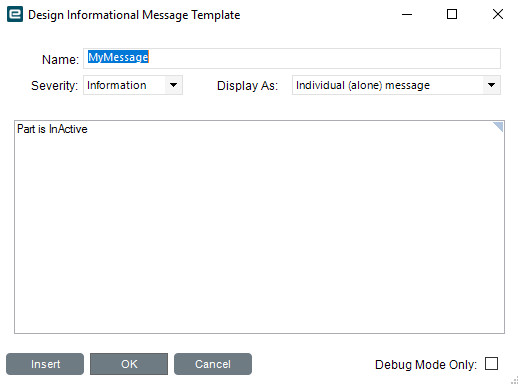
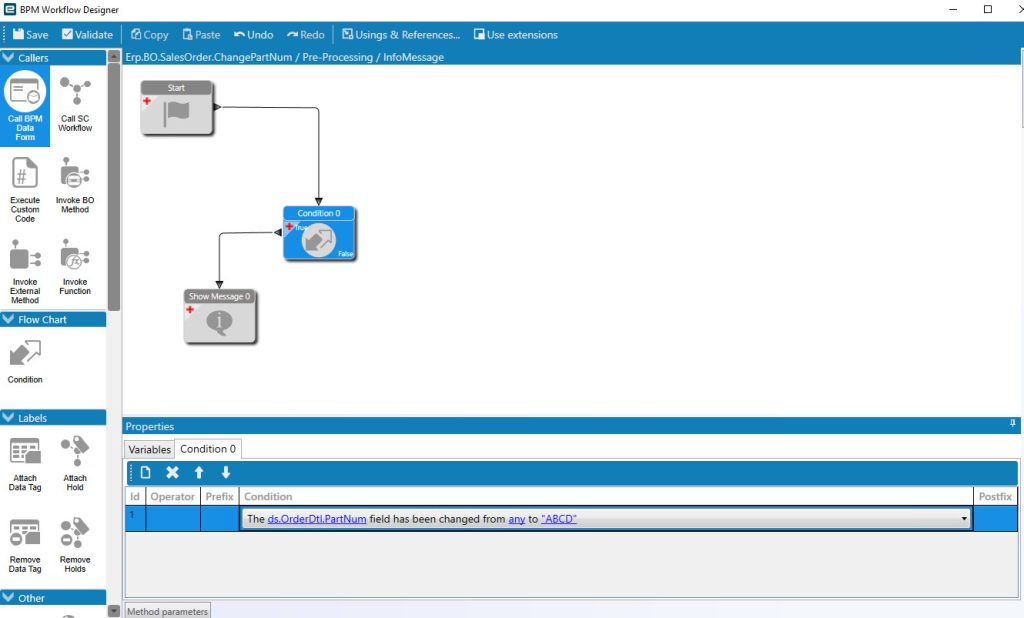
5. Use BPMs to Prevent Duplication Across Modules
Data duplication is one of the most common threats to ERP data quality. Use BPMs to scan for existing values and prevent duplicates.
Example Use Case: Blocking Duplicate Part Numbers
Module: Inventory Management
Objective: Prevent entry of duplicate part numbers, even if part is inactive or unused.
BPM Action:
- Check Part table for existing values
- Use
Raise Exceptionif match is found
6. Build Audit Logs with User Actions
Epicor BPMs can be used to log specific user actions to a User-Defined Table (UD Table). This allows you to trace who changed what and when—useful for both compliance and troubleshooting.
Suggested Audit Log Fields:
- User ID
- Timestamp
- Module
- Field Changed
- Old Value / New Value
This technique improves traceability across Finance, Operations, and HR.
7. Combine BPMs with User Codes and UD Fields for Contextual Rules
Sometimes default Epicor fields aren’t enough. By using User Codes or User-Defined Fields, you can create more nuanced rules that adapt to your business processes.
Example Use Case: Varying Approval Requirements by Department
Module: Purchasing
Objective: Require different levels of approval for different departments.
BPM Action:
- Use a UD field for Department Code
- Apply conditional logic to route approvals accordingly
8. Set Up Tiered Validations for Complex Workflows
For more complex workflows—such as multi-step project billing or serialized inventory—you can layer multiple BPMs that each validate a portion of the transaction.
Example: Multi-Tier Checks for Service Orders
- Tier 1: Validate Technician Assignment
- Tier 2: Check warranty status
- Tier 3: Validate pricing group
Each BPM handles a single rule but contributes to end-to-end integrity.
9. Don’t Over-Automate: When to Avoid Using BPMs
While BPMs are powerful, excessive or poorly designed BPMs can create performance issues and frustrate users.
When to Avoid:
- When rules are better handled in master data setup
- When frequent changes are expected and hard-coded logic could break
- When multiple BPMs conflict with each other or create loops
10. Test and Monitor Your BPMs Regularly
Once deployed, Epicor BPMs should be tested and monitored, especially during:
- System upgrades
- Module changes
- Business process changes
- Performance reviews
Use Epicor’s tracing tools, logs, and sandbox testing to avoid introducing bottlenecks or blocking valid transactions.
Final Thoughts
Enforcing data integrity across modules in Epicor ERP doesn’t require expensive customizations or risky code. With smart, well-structured BPMs, organizations can maintain cleaner records, automate validations, and reduce costly errors across departments.
At Epicforce Tech, our goal is to help businesses get the most value from their ERP systems by using proven tools like Epicor BPMs in a sustainable and scalable way. Our consultants focus on enabling internal teams through best practices, training, and support that keeps your system clean, efficient, and ready for growth.
If your team is struggling with cross-module data inconsistencies or looking to optimize how Epicor BPMs are deployed, we’re here to help. Reach out to us for a conversation no pressure, just problem-solving.